First Chip Resilient to Hardware-Level Threats:
Untrusted Fabrication and Reverse-Engineering
October 2017
Do you think you can break our defense? We welcome attackers!
All information about this chip except for the secret key is available here.
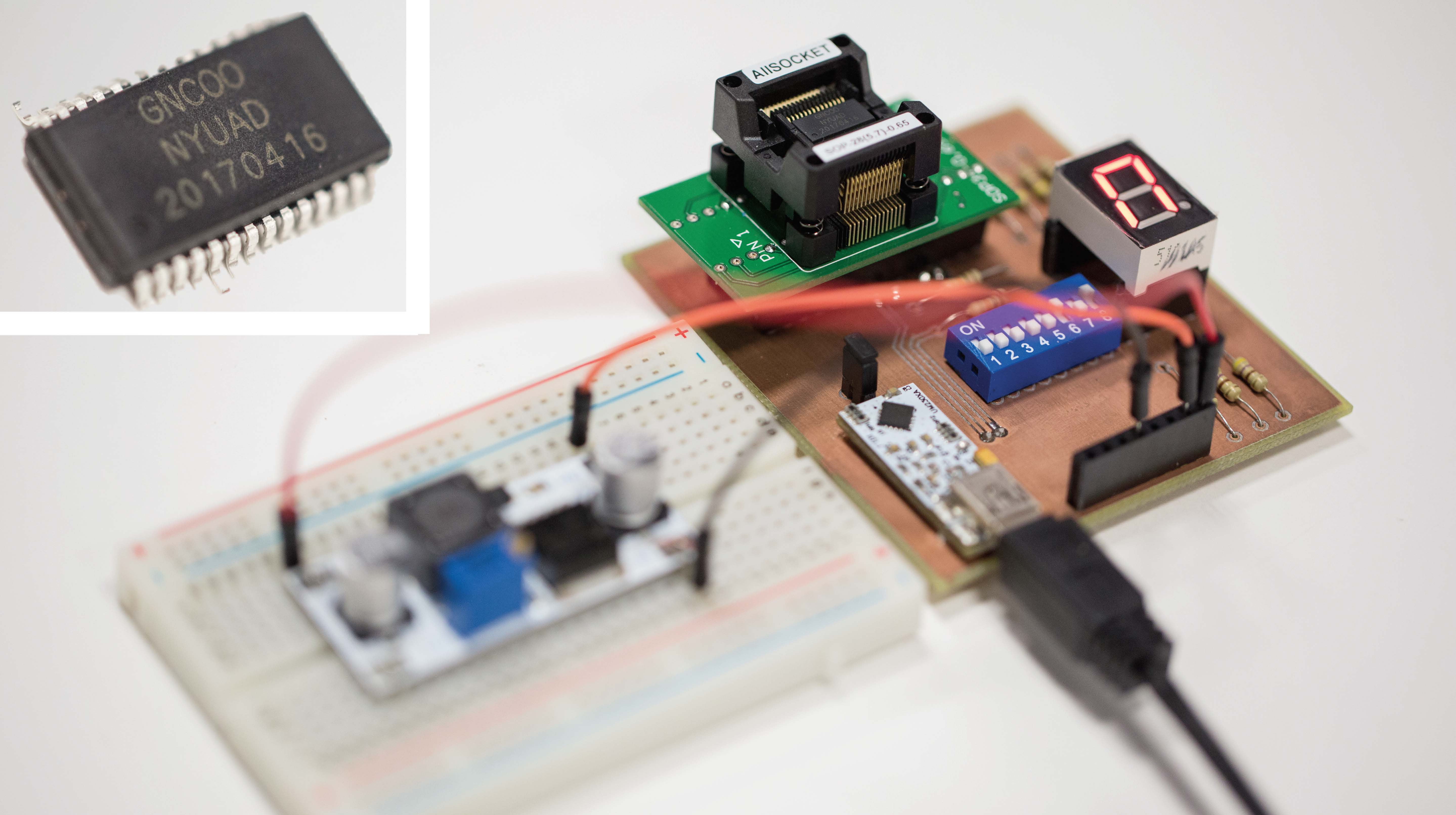
What’s every chip company’s worst nightmare?
Many design companies such as NVidia, Apple, Qualcomm, etc., design their chip and then have them manufactured by third-party fabrication facilities, somewhere in Taiwan, China, etc. They worry about their chip design details being stolen – we refer to this as Intellectual Property piracy – or their chips being tampered with via small modifications at the fabrication facility in the form of hardware Trojans. These Trojans may for instance disable a chip while it is performing a safety-critical operation, or may leak information while the chip is processing or communicating secretive information.
Our solution for this:
Our lab designed the chip above. This is a logic-locked chip with an ARM microprocessor inside. We received the high level design architecture from ARM, a UK-based microprocessor design company, and modified it using our software to implement our logic locking. We had the chips manufactured in the Singapore facilities of GlobalFoundries in 65 nm.
In this chip, some of the microprocessor controller units have been logic-locked using Stripped Functionality Logic Locking (SFLL), which we’ll present at ACM Computer and Communications Security (CCS) 2017. Our lab, in collaboration with Prof Jeyavijayan Rajendran from University of Texas at Dallas, gradually developed SFLL over years of research on logic locking.
How is this chip different than a regular chip?
Traditionally, security features are implemented at the software or system levels; for the first time, we have security implemented at the lowest possible level, the hardware level. This is quite important because if the hardware is compromised, there is no software or system security fix.
This chip has physical locks implemented as part of its hardware design, hence called a logic-locked chip. This chip can be unlocked only by loading the secret binary key on its memory. Without it, the chip will not work. It will simply hang. Only when the secret key has been loaded, it does what it is supposed to do and executes the program loaded on its memory.
We designed this in our lab and had them manufactured in Singapore – which is exactly what major chip companies do – but logic locking thwarts the kind of threats that chip design companies face.
- These logic-locked chips are useless without the secret key; so only the authorized users can use them.
- These chips can’t be reverse engineered. No one will be able to duplicate the design even if they were to get a hold of the final chip because the locks are implemented as part of the design. The hardware implementation only shows part of the design – that’s what the reverse engineers would see; the missing part is dictated by the value secret key. Without the knowledge of the secret key, reverse engineers would thus be missing the crucial part of the picture.
Does this solution apply to only microprocessor chips?
The locked microprocessor chip, shown above, has been used as a proof-of-concept. We can render any digital chip resilient to untrusted fabrication and reverse engineering. For this, we need to apply our logic locking software on its hardware design; the logic-locked design will then be protected from hardware-level threats.
Acknowledgement: This chip fabrication project was part of the TwinLab initiative and has been sponsored by New York University Abu Dhabi Institute, the Center for Cyber Security in Abu Dhabi (CCS-AD), and GlobalFoundries. Our logic locking research that led to the development of SFLL, which was used in this chip, has been sponsored by US National Science Foundation.
