Design-for-Trust Techniques
Rethinking Split Manufacturing: An Information-Theoretic Approach with Secure Layout Techniques
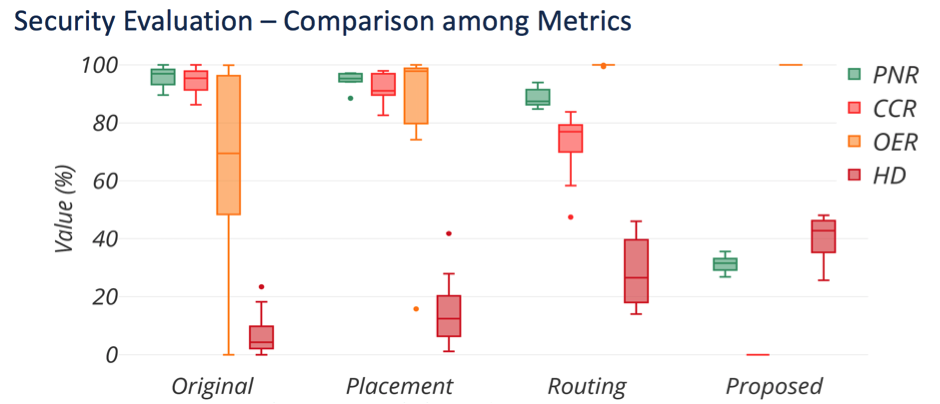
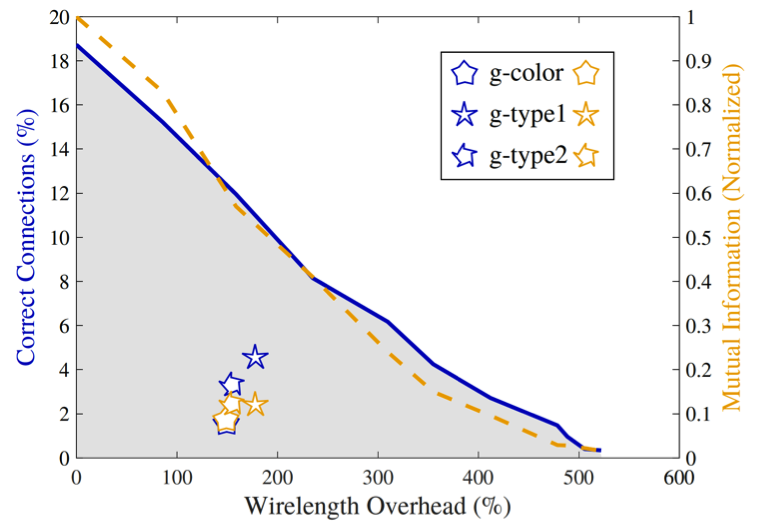
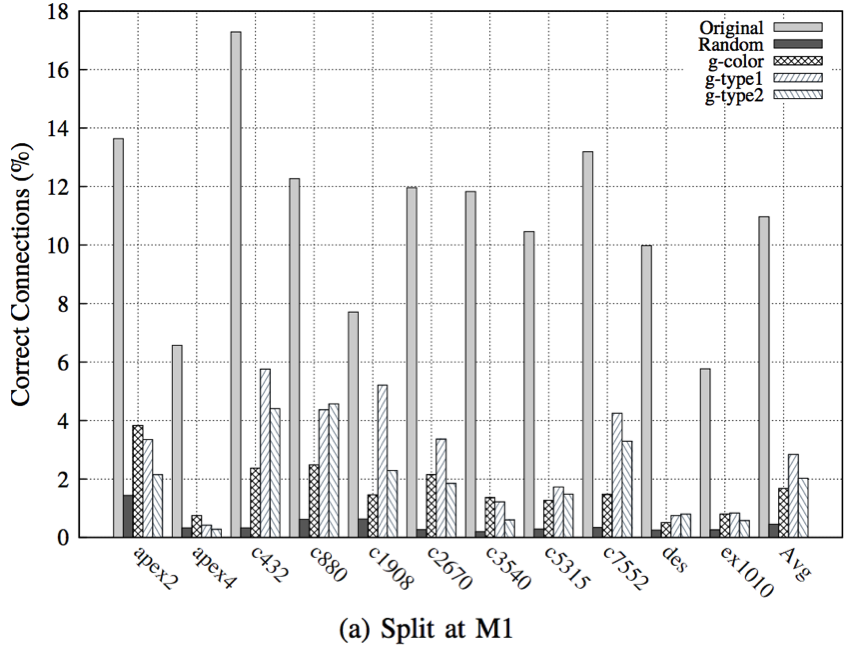
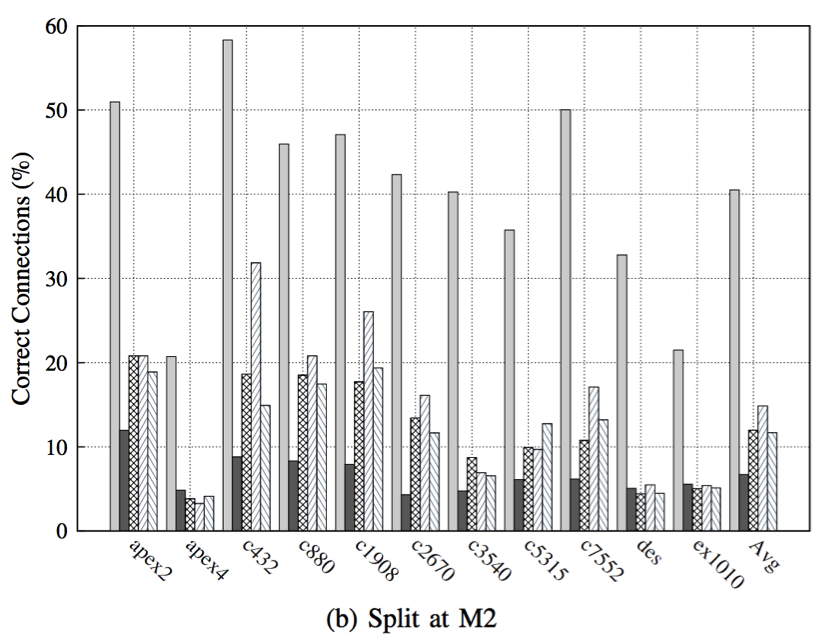
In this work, we present two practical layout techniques towards secure split manufacturing: (i) gate-level graph coloring and (ii) clustering of same-type gates. We also provide—for the first time—a theoretical framework for quantifying the layout-level resilience against any proximity-induced information leakage. Towards this end, we leverage the notion of mutual information. Overall, our placement-centric protection schemes offer superior resilience against proximity attacks which is observed by lowering the success rate of the attack by 5.27x, 3.19x, and 1.73x while splitting at M1, M2, and M3, respectively, when compared to unprotected layouts.
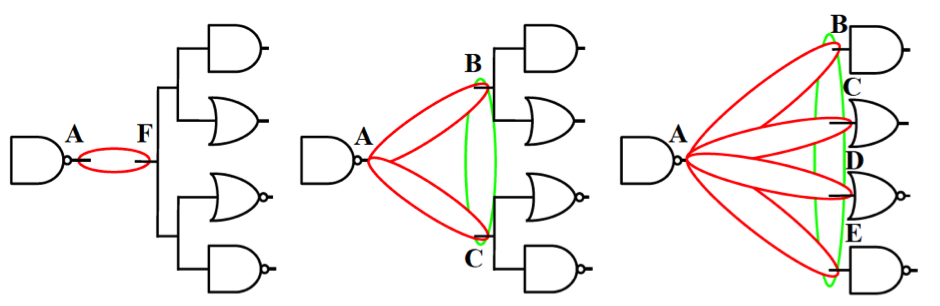
Gate-level graph coloring
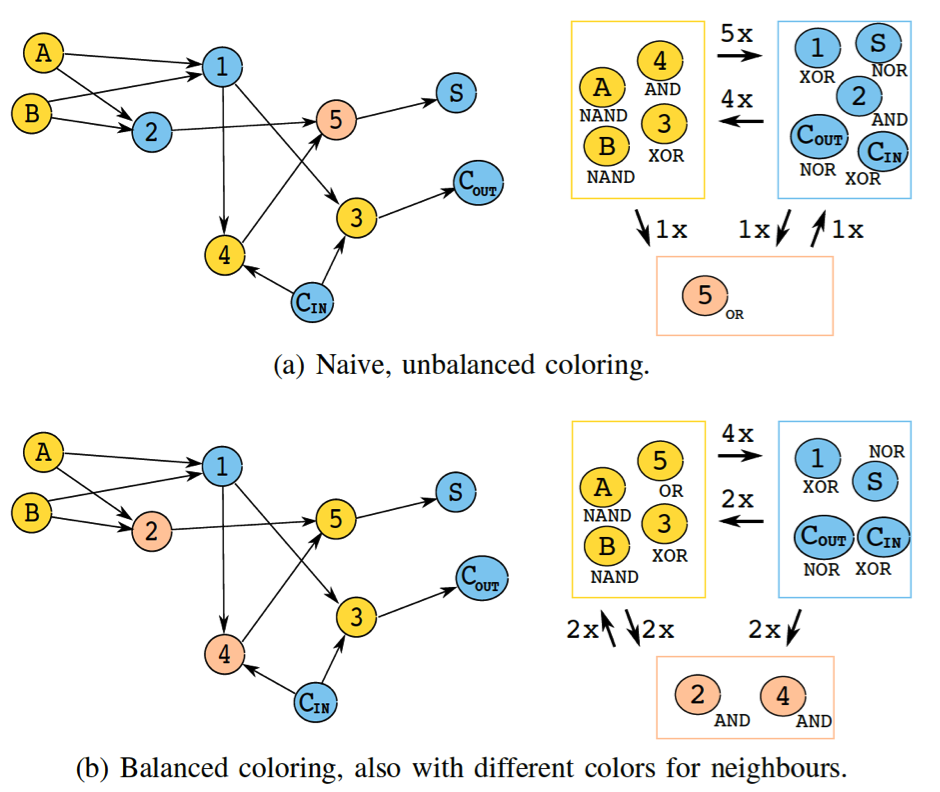
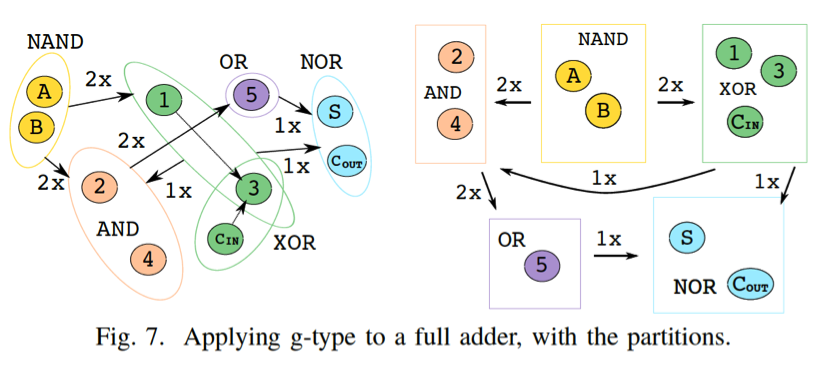
Here we leverage graph coloring to hide the connectivity information; coloring a netlist mandates that there are no connections remaining between gates of the same color. The “colored netlist” is then partitioned by clustering all cells of same colors together and the placement of cells is confined within their respective cluster regions.
Clustering of same-type gates
This technique (a.k.a. g-security) comes in two flavors—we either consider (i) only the functionality of the gates (g-type1), or (ii) both the functionality of the gates as well as the number of their inputs (g-type2). That is, for g-type2 we do differentiate between a 2-input NAND gate and a 3-input NAND gate. Doing so is motivated by our experimental results which indicate that utilizing more partitions renders a design more resilient against proximity attacks in practice.
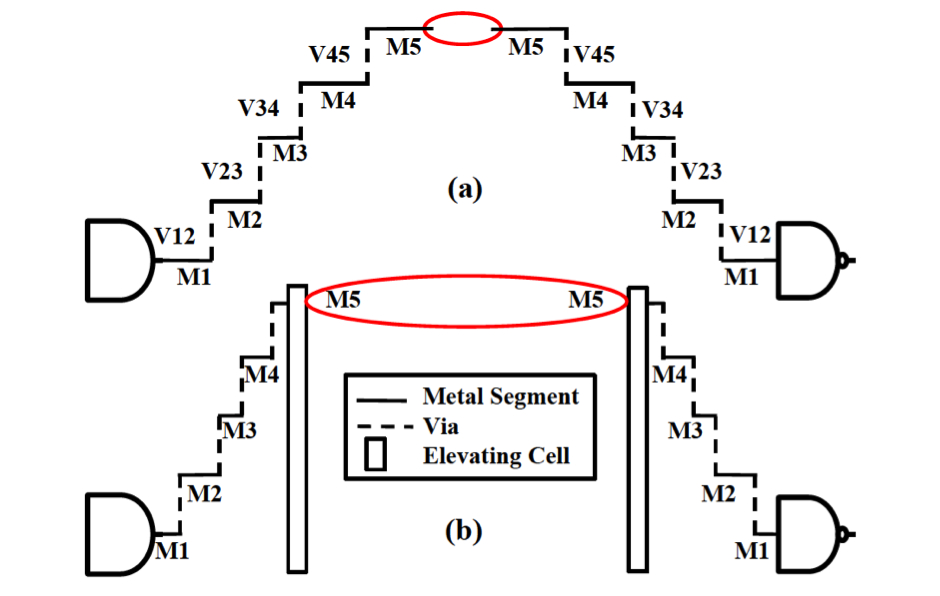
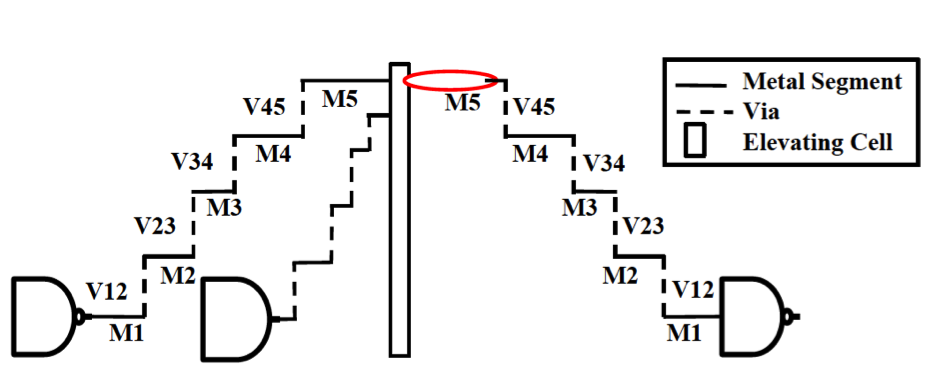
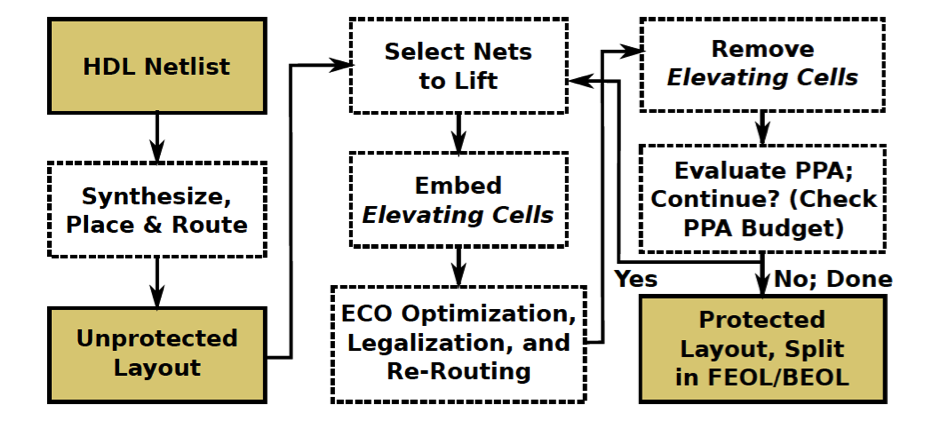
Concerted Wire Lifting: Enabling Secure and Cost-Effective Split Manufacturing
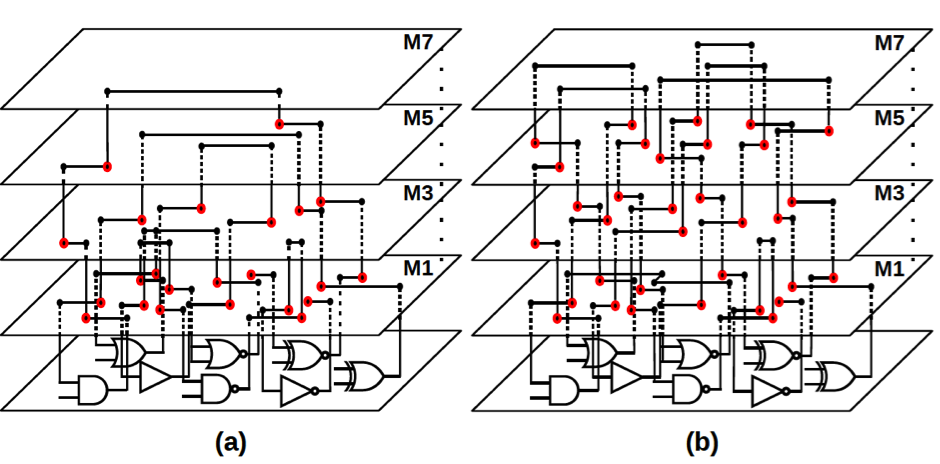
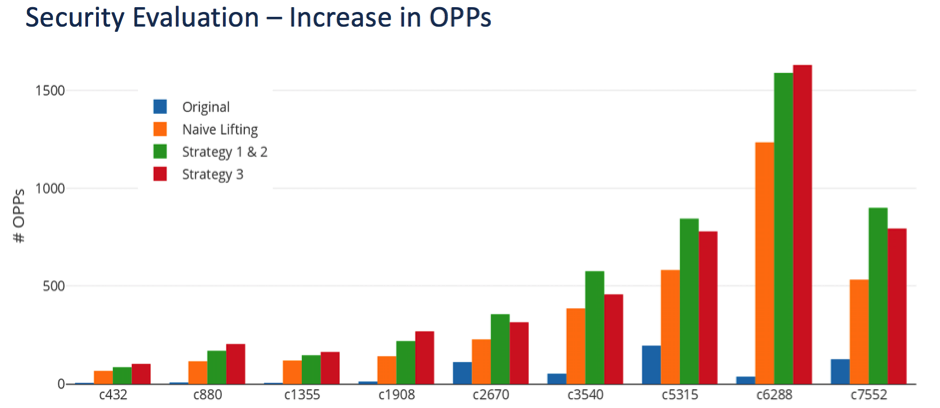
Strategy 1: Lifting High-fanout Nets (HiFONs)