Design-for-Secure-Testability
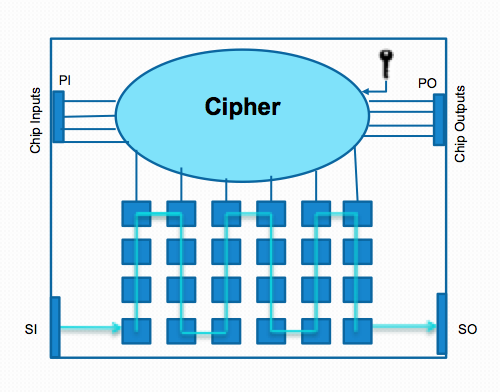
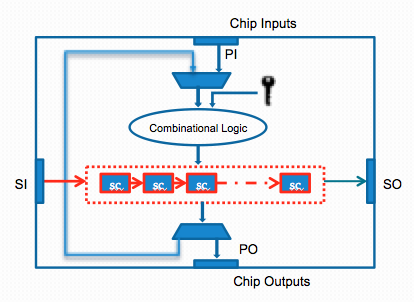
Scan is NOT Secure
While testing is required to screen out defective Integrated Circuits (ICs), any design effort to improve testability may compromise the security of the ICs. To enhance the testability, the test infrastructure provides internal access to the IC. However, an attacker can leverage the test mode to hack into secure-critical ICs. An IC may embed a secret key used to perform on-chip encryption/decryption, or a microprocessor may have an Intellectual Property (IP) instruction set hardcoded into its ROM; such security-critical data must be protected from attacks that misuse test infrastructure.
While scan delivers the desired access into flip flops of the design, it also reveals the intermediate computations within a security-critical chip. In-field testing and debug is thus enabled at the expense of potential security compromise. Access to scan chains can be misused by an attacker to leak data that can infer on-chip secret information; this attack is known as scan-based side-channel attack, where the attacker applies plaintext input from the primary inputs in the functional mode, and then switches to the test mode to shift out the intermediate results through the scan interface.
Scan-based side channel attack relies on the condition that the intermediate results should be preserved upon a switch between the normal mode and the test mode. However, the widely used simple mode-reset countermeasure, i.e., an automatic reset operation upon a switch between the normal mode and the test mode, successfully thwarts these attacks.

The mode-reset countermeasure can only be circumvented if the scan attack remains in the test mode. In the presence of boundary scan DfT, however, the attacker has no direct access to the primary inputs in the test mode. Rather, the attacker has only access to the scan input pins to feed the cipher round register.
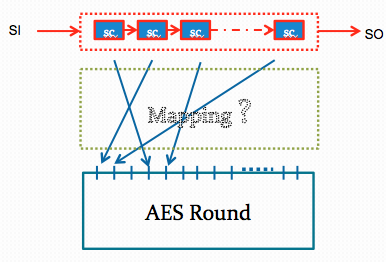
Also, the mapping between scan cells to round registers is unknown as the physical placement tools decide how these flip-flops are connected. We propose an attack, Test-Mode-Only attack, that uses the JTAG port and the basic test capabilities. The scan-attack comprises only shift and capture operations, all performed within the test mode, in order to first identify the mapping between the registers and the scan cells, and next to infer the secret key from the intermediate results.
Test-mode-only attack for basic scan architecture can identify the unknown mapping between the scan cells and the inputs of the AES by creating test vectors to launch the desired bit-flips and observing their effect on the output bits as we show in our papers c72, c73, c79, c84, c85, c86, and c89.
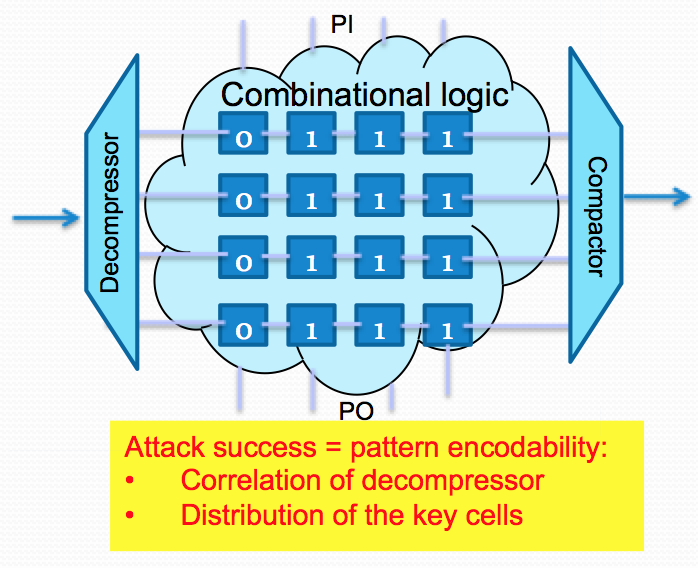
In contemporary test infrastructures that support scan compression, due to the correlation induced by the stimulus decompressor, the attacker may no longer be able to apply the desired test patterns to launch the desired bit-flips; a single bit-flip may trigger an unwanted bit-flip in other locations, resulting in ambiguous or incorrect deductions in the scan attack. A stimulus decompressor and a response
compactor thus end up acting as a natural fortuitous countermeasure for the proposed test-mode-only attacks as they reside on the scan path, further complicating the test-mode-only attack.
In our work in c81, c82, c83, j43, and j51, we identified the conditions for a successful attack in the presence of a scan decompressor and a compactor, and developed countermeasures (decompressor output swapping and scan cell swapping) to ensure that these conditions are never met. The techniques we propose deliver design-for-secure-testability.
