Research Areas
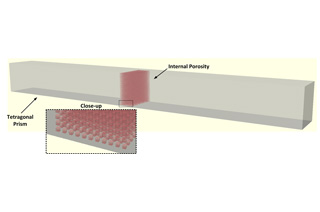
Additive Manufacturing Cyber Security
Additive manufacturing (AM), or “3D printing,” is emerging as the next industrial revolution. As the manufacturing time, quality, and cost associated with AM continue to improve, more and more businesses and consumers are adopting this technology.
Read More
Some of the key benefits of AM include customizing products, localizing production and reducing logistics. Due to these and numerous other benefits, AM is enabling a globally distributed manufacturing process and supply chain spanning multiple parties, and hence raises concerns about the reliability of the manufactured product. Outsourcing parts of the process to potentially untrusted parties raises security concerns, as malicious design modifications can impact the structural integrity of the manufactured 3D geometries. To address this problem, CCS introduced a novel compiler that allows reverse engineering G-code toolpaths (i.e., machine commands describing how a geometry is printed) to reconstruct a close approximation of the original 3D object.
For more details please visit the lab sites: MoMA Lab
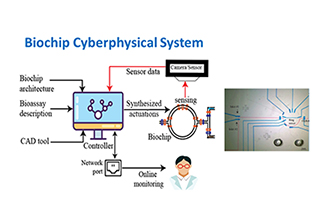
Biochip Security and Cyber Biosecurity
Security and trustworthiness of biochips are becoming increasingly important as they are adopted in safety-critical applications like point-of-care diagnosis, drug discovery, and military applications.
Read More
Recent works have shown that microfluidic biochip platforms are highly susceptible to attacks. Specifically, the bioassay implementation on a flow-based microfluidic biochip (FMB) can be reverse engineered using biochip layout images and actuation sequence which could make IP piracy a realistic scenario. This vulnerability is mainly due to the one-to-one correspondence between fluidic operation and valve actuations in the FMB, and online monitoring of the assay execution.
Therefore, for widespread adaptation of the biochips, it is important to devise tools and techniques that protect the bioassay IP from reverse engineering. In the biochip security research at NYUAD, we have developed multi-height microvalves as simple and yet efficient security primitives in order to obfuscate the one-one-to correspondence between fluidic operation and valve actuations. We denote the microvalve as “Trojan valve” that does not block the fluid flow completely.
The 4-channel microfluidic flow controller from Elveflow including the 4 flow rate sensors (MFS) allows us to actuate 4 microfluidic valves in a PDMS microfluidic chip individually and test the Trojan valves to obfuscate the true microfluidic valve operation when running a cell viability assay on chip. The long-term goal of this research thrust is to prevent unwanted intrusions and malicious and harmful attacks into biological processes that could have major ramifications for healthcare, biopharmaceutical, agricultural, and genomics, and future precision medicine.
For more details please visit the lab site

Critical Infrastructure Security
Critical infrastructures are crucial backbones whose physical or virtual assets, systems, and networks are considered vital for the functioning of nations and societies. Our research activities focus on the security of various instances: from cellular communications and aviation systems to industrial control systems.
Read More
- Mobile/cellular networks (4G/5G/6G) and navigation-/aviation-related wireless systems (GPS, ADS-B) are instances of widely deployed critical communication infrastructures that depend on trustworthy information and communication. These systems are hard to fully secure for very different reasons, but targeted attacks have detrimental effects in all cases. We pursue research efforts in highly secured systems on the offensive side, breaking into deployed 4G/5G cellular systems with the goal to point to weaknesses in current systems. Our research has had an impact on standardization activities of bodies like 3GPP and GSMA (typically via their vulnerability disclosure programs). We also conduct defensive research work by developing mechanisms that improve air-traffic related security at the intersection of GPS (Global Positioning System) and ADS-B (Automatic Dependent Surveillance Broadcast). Through our proposed mechanisms, we demonstrate the potential of sensor-based crowdsourcing for attack detection purposes in a rather closed industry sector.
- Industrial control systems (ICS) interconnect, monitor, and control processes in a variety of critical infrastructure sectors such as electric power generation, transmission and distribution, chemical production, oil and gas, refining, and water desalination. Several notable cybersecurity incidents in industrial environments have underlined the lack of depth in security evaluation of industrial devices such as Programmable Logic Controllers (PLC). Modern PLCs are based on widely used microprocessors and deploy commodity operating systems (e.g., ARM on Linux). Thus, threats from the information technology domain can be readily ported to industrial environments. CCS researchers have developed methodologies for ensuring the security of critical infrastructure in the presence of its unique requirements, such as real-time guarantees, limited resources, proprietary tool chains, and availability requirements.
For more details please visit the lab sites: CSP-lab, MoMA lab

Digital Forensics
Digital forensics has emerged to assist law enforcement in the investigation of crimes involving digital technology.
Read More
However, the increase in the amount of data that is subject to forensics analysis in a typical investigation and the proliferation of cloud services are likely to render most of today’s widely deployed digital forensics tools ineffective. Our research is focused on developing efficient and novel evidence extraction, search, attribution, and analysis techniques that will be used by practitioners in the field.

Machine Learning Security
Due to their ability to extract valuable predictions/information from large pools of data as well as classify enormous data (for instance for image recognition, object detection), Machine Learning (ML) algorithms have proliferated in many application domains, including smart and autonomous cyber-physical systems, robotics, healthcare, and finance.
Read More
State-of-the-art ML systems heavily deploy Deep Neural Networks (DNNs), which consist of many layers of connected neurons and provide valuable results though an output layer. However, due to several uncertainties in feature selection, ML algorithms inherently possess several security vulnerabilities, for instance, sensitivity for small input noise and lack of robustness against affine transformations. Several security attacks have been proposed to exploit these security vulnerabilities, that can be largely classified into: (1) Backdoor attacks during the training phase; (2) Adversarial attacks during the inference phase: and (3) Model Stealing attacks.
At CCS, we are investigating different types of security attacks and defense mechanisms for different types of DNNs, as well as for Spiking Neural Networks (SNNs) that claim to be more biologically plausible and exhibit distinct robustness properties. Prominent works include: backdoor attacks and defenses for connected autonomous vehicles, black-box and white-box adversarial attacks on DNNs, decision-based attacks, attacks on dynamic vision sensors and SNNs, analyzing the tolerance of SNN parameters. We also look at the security and robustness of DNNs from a formal perspective. Prominent works in this direction include input noise tolerance, bias analysis and un-biasing of DNNs, and formal analysis and verification of DNNs using model checking. To develop robust DNN models, our prominent works include security-aware neural architecture search, encryption for DNNs, etc.
For more details please visit the lab site
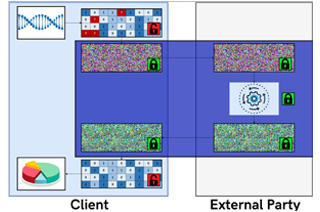
Privacy-Enhancing Technologies & Encrypted Computation
Encrypted data-in-transit (e.g., HTTPS) or encrypted data-at-rest (e.g., encrypted hard-disks) schemes provide sufficient cryptographic guarantees in the battle to protect users’ privacy.
Read More
Snowden’s dissemination of NSA practices revealed that employed cryptography is secure. Even nation-state actors cannot break well-established encryption schemes (e.g., RSA, AES, etc.). The unresolved problem is protecting data-in-use: Currently, in order to process data, we need to decrypt, process, and re-encrypt. Consequently, nation-state and other actors target these processing end-points for collecting information. These end-points are regular computers plagued with vulnerabilities, as evident by the proliferation of disclosures of methods to extract information from them (e.g., buffer overflows, stack smashing, rootkits, return-oriented programming, Heartbleed, Spectre, Meltdown, etc.).
For more details please visit the lab sites: MoMA lab, CSP-lab

Smart City Security
The concept of a “Smart City” is an emerging topic of research that is driven by the need to enhance the quality of life of the growing number of inhabitants in urban areas.
Read More
As world urbanization continually grows and the world’s population is expected to increase significantly by 2050, smart cities offer an attractive solution that can contribute to economic growth, increased efficiency of energy and transportation systems, and promote sustainable development. One of the main research challenges that the development of smart cities faces is the assurance that the Cyber-Physical Systems (CPS) that control and monitor the city’s operations are working in a safe, secure and reliable manner. With increased integration between computer systems, physical devices, and multiple data sources, the cyber security of smart cities quickly becomes a multidisciplinary problem that requires novel solutions.
Embracing the motto “we do not have the option of turning away from the future”, CCS-AD has developed a smart city testbed. The purpose of the testbed is to provide a realistic and real-time smart city environment for researchers to perform security evaluations on the equipment. It consists of security-sensitive and potentially vulnerable devices like control systems, smart grid devices, smart sensors/actuators used in intelligent buildings and houses, environmental sensors, networking devices/gateways, and a local server that acts as an Internet-of-Things (IoT) platform. The devices are deployed in Hardware-In-the-Loop (HIL) simulations, using software elements and mathematical models suitable for each application. All of the devices are interconnected and exchange data through the testbed’s networking infrastructure and are monitored and controlled by an IoT platform. The lab space is an open environment, where researchers are welcome to perform studies and evaluate their results in a realistic environment.
For more details please visit the lab sites: MoMA lab, CSP-lab
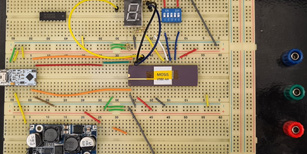
Trusted Hardware Design
The hardware trust research addresses the problem of securing the hardware root of trust against untrusted entities in the distributed chip supply chain.
Read More
Our goal is to equip chip designs with proactive defenses to protect them as they go through stages such as fabrication, testing, and assembly at third-party companies typically residing off-shore. The research challenges are to develop hardware design and software automation solutions that provide protection against threats such as hardware trojans and backdoors, Intellectual Property piracy, and counterfeiting. Example design-for-trust techniques we develop comprise logic locking, split manufacturing, and layout camouflaging. We have also created working prototypes (fabricated chips) by applying some of these techniques at 65 and 55 nanometer technologies. We address these problems in the current as well as the emerging fabrication technologies.
For more details please visit the lab site
Silicon Optical Physically Unclonable Functions
The omnipresent digitalization trend has enabled several related malicious activities, ranging from data theft to disruption of businesses, counterfeiting of devices, and identity fraud, among others.
Read More
Hence, it is essential to implement security schemes and to ensure the reliability and trustworthiness of electronic circuits. However, most PUFs have eventually, at least partially, fallen short of their promises, which are unpredictability, unclonability uniqueness, reproducibility, and tamper resilience. That is because most PUFs directly utilize the underlying microelectronics, but that intrinsic randomness can be limited and may thus be predicted, especially by machine learning. Optical PUFs, are still considered promising. They can derive strong, hard-to-predict randomness independently from microelectronics, by using some kind of “optical token.” We proposed a novel concept for plasmonics-enhanced optical PUFs, or peo-PUFs in short.
For the first time, we leveraged highly nonlinear phenomena by surface plasmons arising from nanoparticles arranged randomly on top of the resonator. This study highlights the good potential of peo-PUFs. Our future work is to focus on the fabrication and characterization of such PUFs. We also proposed a simple authentication scheme, based on the secure keys and some related helper data. The concept can be directly integrated into any silicon device, thus can provide better resilience than prior external PUFs.
For more details please visit the lab site
